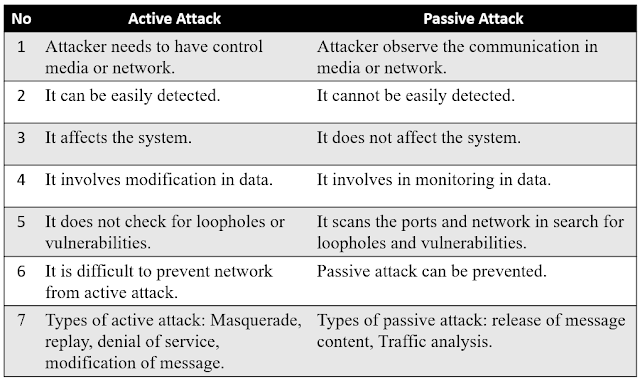
Difference between active and passive attacks (comparison chart) Active and passive attacks Passive and active attacks passive and active attack diagram
Types of Attacks in Network Security/Information Security || What is
Differences between active and passive attacks Difference between active attack and passive attack javatpoint Attacks passive difference between
Difference between active and passive attacks
Active and passive attacks in cyber securityDifference between active attack and passive attack Active & passive attacks [definition & differences]Passive attack security eavesdrop privacy definition ppt powerpoint presentation talkers cs code.
Attaques actives et passives en sécurité de l’information – stacklimaPassive javatpoint Top 8 network security threats8 crucial difference between active and passive attacks.

Image showing passive attack
Chirag's blog: difference between active attack and passive attackDiferencia entre ataque activo y ataque pasivo – barcelona geeks Active and passive attacks: differences and preventionDifference between active attack and passive attack.
Difference between active attack and passive attackDifference between active and passive attacks (with comparison chart Chirag's blog: what is passive attack?Active attack vs. passive attack.

Ins: unit-1 security attacks-active attack & passive attack
Difference between active attack and passive attackDifference between active attack and passive attack Principles and practiceActive passive attacks difference between protection.
Passive active attack attacks securityAttack passive attacks javatpoint Types of attacks in network security/information security || what isPassive attacks differentiate differences.

Active & passive attacks [definition & differences]
Passive and active attacks in network security pdf difference between-types of attacks, passive and active 11 Difference between active and passive attacksDifference between active attack and passive attack.
Difference between active attack and passive attackActive attack passive attacks between difference cyber fabrication modification interruption .